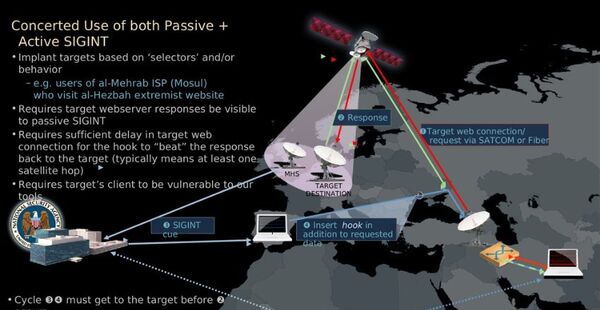
According to the documents released by Der Spiegel, the NSA also effectively hijack the compromised computers. Those computers infected with botnet malware do the NSA’s bidding and attack other target computers to which the agency wants access.
“We found a few instances where there were NK officials with SK implants on their boxes, so we got on the exfil [data exfiltration] points, and sucked back the data,” the staffer wrote. “However, some of the individuals that SK was targeting were also part of the NK CNE program. So I guess that would be the fifth party collect you were talking about.”
Some accounts also show NSA officials used the malware to destroy the contents of target computers, as well.
Another advantage for the NSA: If the spying malware is discovered, it will likely be traced back to the hijacked computer rather than back to the NSA.