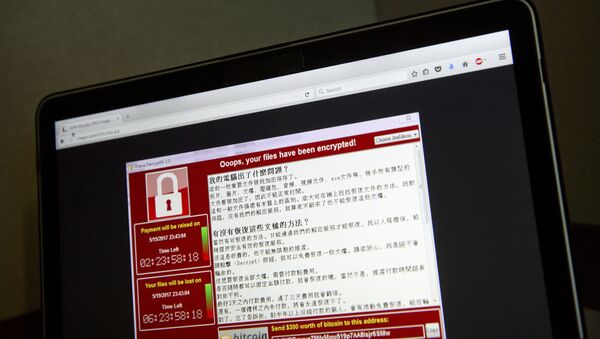
On Friday, computer systems across the world were attacked by hackers in an attack dubbed WannaCry," which uses an NSA exploit codenamed EternalBlue that was one of several tools leaked by the Shadow Brokers last month.
The tool exploits a vulnerability in Microsoft's Server Message Block which allows attackers to crash systems with a denial of service attack. After scrambling computer files, the malware demands $300 in Bitcoin to restore documents.
According to Kaspersky Lab, the cyber-attack has hit as many as 74 countries, including Russia, Ukraine and India.
The infections disabled at least 16 hospitals in the UK, Spain's main telecommunication services provider Telefonica, the Russian telecommunications provider Megafon and some Italian universities.
"It's quite effective and quite vicious insofar as it actually disables and paralyses computer systems in quite a dramatic way," Dr. Binoy Kampmark, Senior Lecturer at RMIT University in Melbourne told Radio Sputnik.
"We've already been seeing the vulnerabilities of the system in the last few years. So, for example in 2016 we've already seen aspects of the ransomware being deployed for example against the Hollywood Presbyterian medical center. In that particular instance, $17,000 was requested to regain access to the hospital files. We've also seen attacks on police force systems in Tewksbury, Massachusetts."
"It's not new, [but] it's the scale that is dramatic. So far, the point about this particular system of course is that it's been essentially a re-adapted system from old NSA protocols which are being used and that's one of the most striking things."
"The reality is that these particular systems are going to be used, more will be coming out because this is after all a new frontier … we are set to deal with matters of security in this way, which connect intelligence agencies but also those in the private sector. So, we are concerned essentially about security of data both in a private and a public sense, so we can expect more of that, I'm afraid."
Users of Windows XP or earlier versions of Windows were initially left without a patch. Support for XP, which was released in 2001, ended in 2014.
Windows usually stops supporting earlier versions of software after a decade or more, but in the face of Friday's attack it took the unusual step of issuing a one-time patch for Windows XP, Windows 8, and Windows Server 2003, which are all no longer supported.
"It's the old problem of making sure that the particular computer systems at an organization are actually fire-proofed against this sort of thing. Unfortunately Windows is rather vulnerable and it keeps showing time and time again, whether it's the NSA or a private hacking crew, we tend to face the same problem," Kampmark said.
"The reality of it is that there are system vulnerabilities, the key is to make sure that these things are updated and people are cognizant of the risks in this ever-digital environment and that's one of the things to be mindful of.
Have you heard the news? Sign up to our Telegram channel and we'll keep you up to speed!