In the article, the author outlined six moves that need to be implemented to enhance US cybersecurity capabilities.
First, Stavridis proposed reforms on the governmental level, including increased coordination between agencies in charge of cyber-issues. Currently, there are the NSA, the Department of Homeland Security and the FBI, and coordination leaves much to be desired.
"Six separate centers for cybersecurity are scattered across the government, none of which really has the lead. And perhaps most worrisome, there is no single voice in the president’s cabinet for cybersecurity," Stavridis wrote.
According to him, one cybersecurity agency should be established and a coordinating role in cybersecurity issues should be given to the director of national security.
Third, the NSA and the US Cyber Command should be split, in order to optimize the decision making and management process.
Furthermore, Stavridis proposed increasing cooperation between public agencies and private firms.
"Congress can play an important role here by passing legislation that provides or backs up cyberinsurance, reduces liability for information sharing, and establishes formal private-public bodies, much as is done in other sectors," the article read.
A fifth idea is developing "cyber-education." The author noted that over 70 percent of cyberattacks can be prevented if users follow the basic rules, including changing passwords and avoiding the use of thumb drives from unknown sources.
"This past weekend’s global attack was a harbinger. We have to improve our readiness to respond when the real cyber-Pearl Harbor threatens," Stavridis concluded.
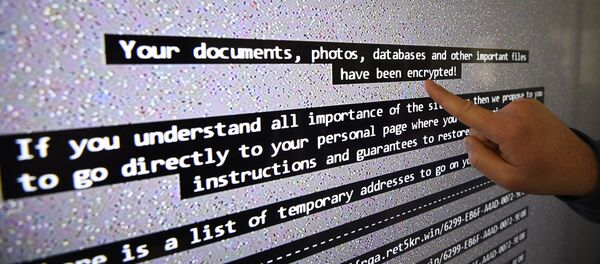
The large-scale cyberattack which has compromised organizations in dozens of countries worldwide started Friday, and, according to the Kaspersky Lab IT company, the attacks were carried out using a specific ransomware called WannaCry.
On Sunday, Europol Executive Director Rob Wainwright said that 200,000 users in 150 countries, including businesses and large corporations, were subjected to the attack.
Among other institutions and organizations, the malicious software affected the UK public health system NHS, the German state rail company Deutsche Bahn, the Russian Interior Ministry and banks. The virus blocked computers with messages flashing on the screen demanding money to remove the restriction.
Never miss a story again — sign up to our Telegram channel and we'll keep you up to speed!