The Petya ransomware ("Petya" is Russian and Ukrainian for the name "Peter" or "Pete") affected operations of the world's largest companies on the 27th June, and its algorithm was similar to the much-publicised WannaCry attacks in May. The malware attacked computer systems of affected businesses and entities, completely paralysing computer networks and demanding a ransom from their owners for access to be restored.
The Petya ransomware is very similar to the WannaCry episode also in that the hackers used the same code, classified by the US National Security Agency (NSA) as "Eternal Blue." The wider spread of the virus was achieved by two other mechanisms, specialists of the cybersecurity firm, Symantec, said.
The Petya cyberattack, on its part, has turned out to be a major economic challenge and has entailed significant operational losses for businesses around the globe, and also might have affected the security systems at the nuclear disaster site in Chernobyl, Ukraine.
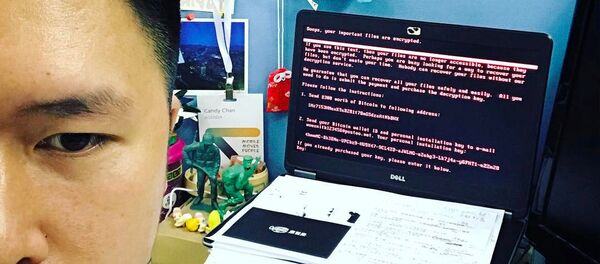
"Your files are no longer accessible because they have been encrypted," the Petya ransomware says, demanding $300 in Bitcoin cryptocurrency for the access to computers in a network. The Petya-caused turmoil continued on Wednesday June 28, thus far having affected computer systems and operation of such major businesses as container ship operator Maersk, real estate branch of the French bank BNP Paribas, a Cadbury confectionary facility in Australia, Russia's oil giant Rosneft and industrial metals producer Evraz, and a handful of Ukrainian banks and governmental institutions.
The Petya attack was first reported in Ukraine, hence the Russian-Ukrainian name for the ransomware, with many Ukrainian banks experiencing cash dispenser shutdowns, the work of many governmental offices paralysed, state-owned power supply company experiencing disruptions. Kyiv's underground rail system and airports were also hit by the cyberattack, whilst the radiation security systems of Chernobyl were down as well, causing workers to manually measure the radiation levels on site.
Next, the New Jersey-based food producer Mondelez, the aforementioned Maersk, the law firm DLA Piper, and hospitals in Pittsburgh, PA reported being attacked.
The attack is "a bit like a flu epidemic in winter," Nicolas Duvinage, director of the French military cybersecurity agency said. "We will get many of these viral attack waves in coming months."
Cyberattacks are becoming an increasingly prominent risk to business activity, adding to the intensified political woes that have entailed large-scale hacks over the past 2-3 years. The situation is exacerbated by the fact that there is no international coordination on tackling such challenges, meaning that cybersecurity will add to business expenditures in the coming years as governmental anti-hacker agencies are not always able to prevent the multi-million losses that such viruses might do in damages to the private sector of the economy.
"The international cyberattack hit our non-bank subsidiary, Real Estate. The necessary measures have been taken to rapidly contain the attack," BNP Paribas, the French bank, said.
One of the interesting aspects of the Petya attack is that the malware targeted primarily the Microsoft Windows-powered computers, blocking access to the hard drives by encrypting and/or overwriting the files. Typically, a solution in ransomware situations is backup recovery, but nonetheless, the computer networks affected are forced to idle for hours. In the absence or proper international coordination on cybersecurity between governmental agencies, private-sector entities will have to ramp up their cybersecurity investment, which is becoming another prominent liability and a burden to business activity and economic growth.