A Twitter employee collaborated with hackers to take over blue-ticked accounts across the platform on Wednesday, Vice reported, citing two sources from a hacking community responsible for the attack. It also provided leaked screenshots obtained by Vice’s Motherboard allegedly proving the deed.
According to the sources cited by the outlet, the Twitter insider was paid to “literally” do “all the work” for the hackers. The employee could have provided hackers with access to a necessary tool which helped them carry out the attack or simply hijacked the account by himself or herself, Vice said, citing the comments of a Twitter spokesperson.
So far, the Twitter Support team has only publicly stated that: “We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools.”
We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf. We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.
— Twitter Support (@TwitterSupport) July 16, 2020
Screenshots of Internal User Tool Get Deleted on Twitter
Vice’s Motherboard provided screenshots, allegedly proving that celebrity-held accounts were hijacked using an internal administration tool at Twitter. One of the screenshots shows the internal panel of a cryptocurrency-exchange Binance account that was also hacked on Wednesday. The media notes that the accounts could have been compromised through a change of the email address linked to them with the help of an internal tool.
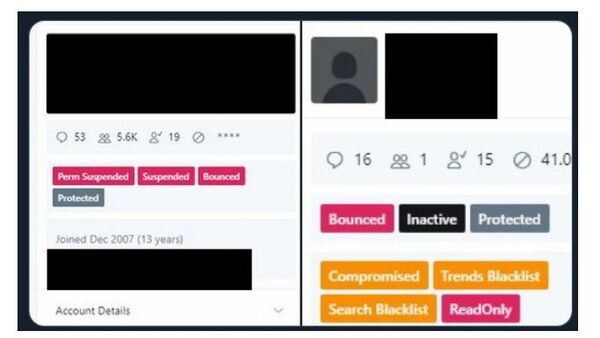
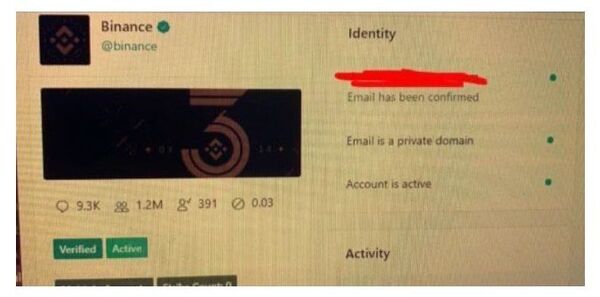
However, the screenshots of the internal panel and hacked accounts shared around the social media have been widely deleted by Twitter, while users sharing such posts were suspended, as the posts apparently violated the company's rules. Vice argued that this has happened to the post by Under The Breach, a data monitoring service. Twitter allegedly deleted its post with a screenshot showing the image of the panel and suspended the account for 12 hours.
According to Vice, a Twitter spokesperson explained the recent development in relation to a removal of tweets containing screenshots of the panel and details of the users' accounts in an email to Motherboard, by saying that "as per our rules, we're taking action on any private, personal information shared in Tweets".
Twitter has been repeatedly criticised for censoring free speech while banning accounts of prominent conservative figures in the past, including those of James Woods and Alex Jones' InfoWars, while also flagging and deleting posts it claimed didn't comply with the company's rules. Its decision to prevent the spreading of screenshots allegedly illustrating the internal source of the attack on Twitter users was also taken with a pinch of salt.
'Cooordinated' Attack on Verified Accounts
On Wednesday, a massive hacker attack targeted a number of high-profile verified accounts on Twitter with a bitcoin scam, including those of SpaceX’s Elon Musk, Bill Gates, presumptive Democratic candidate Joe Biden, former US president Barack Obama and many others, as well as such companies as Apple, Gemini and Binance.
While the investigation is still ongoing, the Twitter Support team notified the users that “significant steps to limit access to internal systems and tools” had been taken.
“We have locked accounts that were compromised and will restore access to the original account owner only when we are certain we can do so securely,” it said.
The Attack 'Will Result in Millions of Dollars of Reputational Damage' for Twitter
“This hack is unlike the normal hacks we usually see”, says Choong-Fook Fong, CEO of Malaysia-based information security consultancy LGMS, arguing that “it is hard to ignore the fact that whatever posted by these accounts actually put a strong influence to the world”.
Fong believes that “the actual vulnerability really lies within Twitter internally” in this case.
“If Twitter is to implement enhanced security policies and procedures, they may want to start implementing it from within Twitter”, Fong adds, suggesting that it is unlikely that the attack will cause any new form of “restrictions” for its users.
For Pierluigi Paganini, Chief Technology Officer at Cybaze, it is still a question as to how the hackers “tricked” a Twitter insider into providing them with access to the internal tool. Paganini says he is open to the possibility of “a unfaithful Twitter employee that received money to grant the access”.
“In this specific case the problem is related to the management of the platform”, Paganini says.
Professor of Cyber Security at Ulster University Kevin Curran agrees that the hacking attack was “extremely low tech”.
“It just required a very focused individual(s) to befriend and bribe insiders to reset accounts”, the scholar argues, while saying that “this is one of the most difficult cyberattacks to defend against” but “some sort of artificial intelligence” might help to prevent these kind of attacks in the future.
Despite the fact that Twitter stock dropped over 5% at pre-market trading on Thursday following the hacking attack, corporate advisor on cybersecurity Rich Tehrani suggests that the development will have “no lasting damage to Twitter’s stock”. That said, it is an “embarrassing incident which reduces the trust people have in Twitter’s brand”, he adds.
“It will result in millions of dollars of reputational damage which could have been prevented”, Tehrani concludes.
Charles R. Smith, CEO Software Inc expert and encryption security programmer believes that in terms of stock value the hack will have some effect on Twitter itself "since the company does not take information security seriously".
"The hack was directed at the internal IT staff and clearly shows that the training and loyalty of Twitter employees to basic security and corporate integrity is lacking. The result was a classic 'insider' attack - where the willing or unwilling participation of company employees was critical to the success of the event. [...] The poor security culture is a reflection of the ownership and direction taken from the top down at Twitter which seems to place politics above the integrity of customer data".



