The Intercept points out that contrary to official statements that the drone strike campaigns are "directed at high-level terrorists who pose an imminent threat to the United States," the study "hints at the use of so-called signature strikes against unknown individuals exhibiting suspicious behavior," plus additional strikes carried out by the CIA with its own target selection and decision-making standards.
Emphasizing that "the Obama administration has been loath to declassify even the legal rationale for drone strikes," the online paper notes that the leaked documents help to uncover important details on the bureaucratic structure behind the attacks.
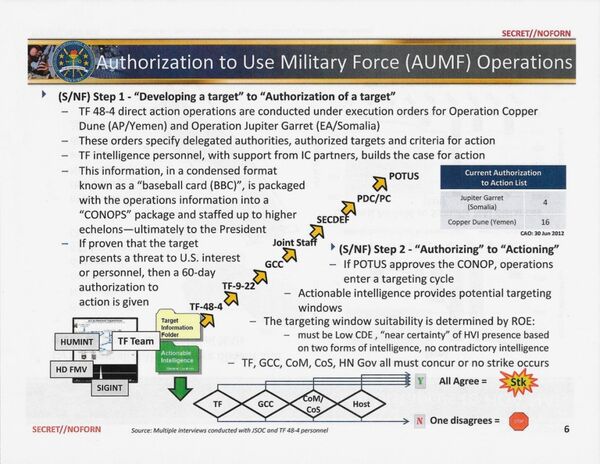
Apparently, the process behind the US military's attacks is broken up into two simple, logical steps, from 'developing and authorizing' the target, to 'authorizing and actioning' (i.e. striking).
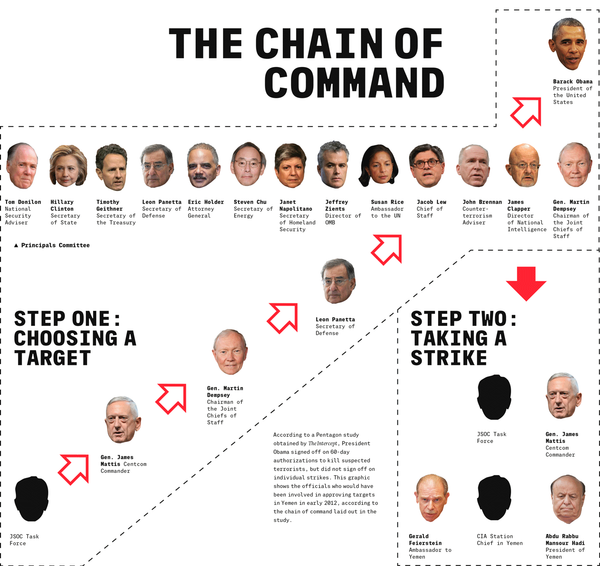
The slide shows that US military intelligence personnel compile information on the suspicious individuals being tracked into "a condensed format known as a 'baseball card', packed with operations information into a 'CONOPS' package and staffed up to higher echelons – ultimately to the president."
The 'intel package' moves from the Join Special Operations Command task forces tracking the individual in question, up to regional command (Centcom in Yemen, Africom in Somalia), and then further, to the Joint Chiefs, and the secretary of defense. Analyzed by the Principals Committee of the National Security Council, a circle of top advisors (including members of the cabinet), and their advisors, the target ends up on the president's desk.
Commenting on the process, which also includes getting formal permission from the country in which the strikes take place, The Intercept points out that while standard practice is to inform leaders, either shortly before or during the operation, it remains unclear what would happen if a country were to formally reject the idea of American drones carrying out operations on its territory, since it hasn't yet occurred.
However, The Intercept does note that today, with the Abdu Rabbu Mansour Hadi regime toppled by Houthi rebels and being bombarded by Saudi warplanes, "administration lawyers do not seem worried about asking permission to carry out drone strikes." A former Yemeni official speaking to the paper suggested that "they don't even bother telling anyone," since "there is really no one in charge to tell." This is probably a sentiment which the fledgling Houthi government in Yemen might contest.
The Intercept confirms that dark spots remain over the strike criteria, noting that the leaked Pentagon report does not actually give any "extensive description of the criteria for approving a target."
Furthermore, "the slide illustrating the chain of approval makes no mention of evaluating options for capture. It may be implied that those discussions are part of the target development process, but the omission reflects the brute facts beneath the Obama administration's stated preference for capture: Detention of marked targets is incredibly rare."
Pointing to the discrepancy between the Pentagon target list (with 20 authorized targets in Yemen and Somalia cited in the Pentagon report by the end of June 2012), and the fact that the US had actually conducted at least 55 drone strikes and other attacks in Yemen between 2011-2012 alone, The Intercept suggested the discrepancy came from the fact that "some of those Yemen strikes were likely carried out by the CIA, which since mid-2011 has flown drones to Yemen from a base in Saudi Arabia and…has its own kill list and rules for strikes."
Finally, in contrast to the guidelines released by the White House in May 2013, which suggested that strikes can only occur "in the absence of civilians," the Pentagon slideshow actually refers to "a low CDE [collateral damage environment]," which means that possible civilian deaths should be limited, but does not completely rule themout. "In contrast to the White House statement, the 'near certainty' standard is not applied to civilians," The Intercept concludes.